Hive Systems Password Table Image/Hive Systems
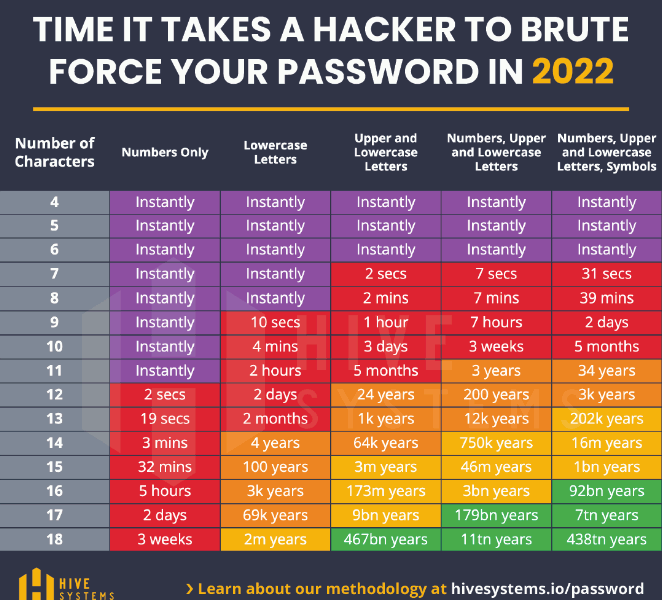
Hive Systems recently updated the Hive Systems Password Table for 2022. The Hive Systems Password Table determines how easy or diffficult for hackers to decipher a password. The Hive Systems Passwords Table has been shared across the internet, social media, the news, and organizations worldwide.
Although the Hive Systems Password Table is a good indicator how secure and uncrackable one’s password is, there are a few caveats to consider regarding the conditions associated with the Hive Systems Password Table:
1. Cracking passwords this way assumes that the attacker has acquired a hash digest of one or more passwords, such as those found in password data breaches on HaveIBeenPwned.
2. The implied attack assumes that MFA is not used or has been bypassed.
3. These metrics assume that passwords are randomly generated. Non-randomly generated passwords are much easier and faster to crack because humans are fairly predictable. As such, the time frames in these tables serve as a “best case” reference point. Passwords that have not been randomly generated would be cracked significantly faster (see above).
4. These metrics assume you’re using a password that has not been part of a breach in the past. Attackers will try hashes to all common and breached passwords before bothering to crack new ones (see above).
5. Hashcat defaults to 999 iterations for PBKDF2 SHA-256 but that doesn’t represent what people use. NIST recommends a minimum of 1000 iterations and sites like LastPass use 100,100 iterations, and 1password uses 100,000 iterations.
6. Hashing is only one step to “cracking.” The second step is looking for matches between the hashed strings and the breached hashed password dataset.
7. These metrics assume a finite “sample space” of 650 characters for password length. We also assumed that the passwords were limited to the character set shown below. If an attacker is confident you wouldn’t use a particular subset of characters – like Cyrillic alphabet characters, for example – the sample space is even smaller, and a given your password could be cracked even faster.